Welcome to Capture Corner
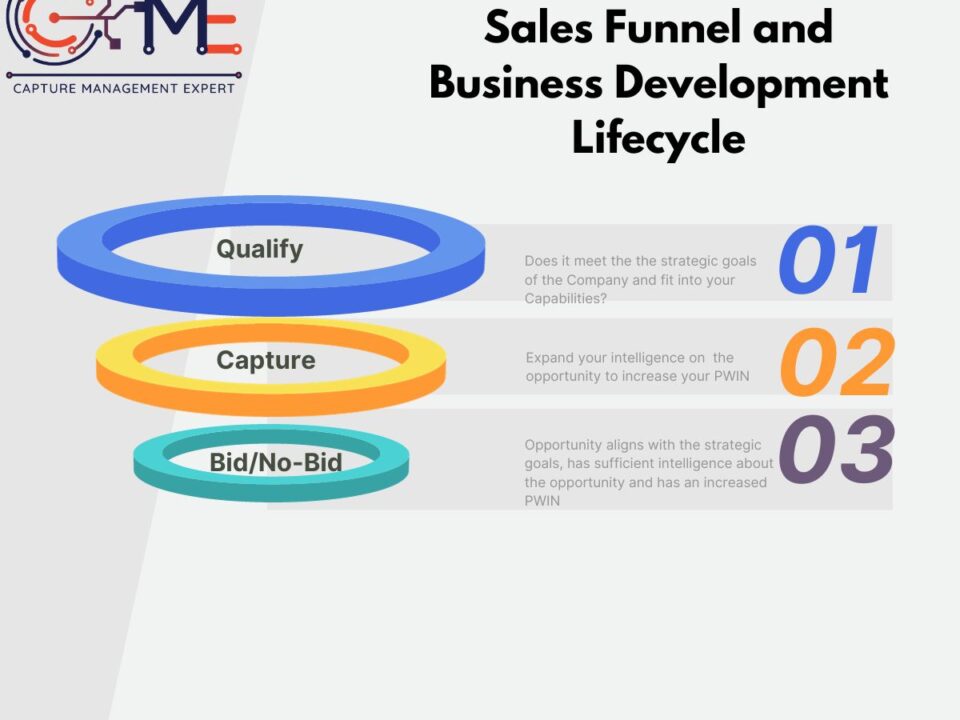
June 28, 2022Business Development Lifecycle
July 12, 2022ZTA
Zero Trust is a framework for securing infrastructure and data for today’s modern digital transformation. It uniquely addresses the modern challenges of today’s business, including securing remote workers, hybrid cloud environments, and ransomware threats. While many vendors have tried to create their own definitions of Zero Trust, there are a number of standards from recognized organizations that can help you align Zero Trust with your organization.
There are only a handful of Active Opportunities focused on Zero Trust published in SAM.GOV There are 140 Inactive notifications about Zero Trust in Sam.Gov. That doesn't mean there aren't more - that is just what is on the surface at SAM.
White House Executive Order 14028 on May 12, 2021, made the zero trust architecture central to the federal security landscape, required agencies better defend against exploits and is driving the transformation of government systems into more secure digital infrastructures.
What Goes into Zero Trust
Identities: people, services and internet-of-things components.
Apps and Services: ensuring appropriate permissions and secure configurations
Data: giving the necessary attributes and encryption to safeguard out in the open
Infrastructure: hardening against attacks on-premises or in the cloud
Networks: establishing controls to segment, monitor, analyze and encrypt end-to-end traffic
Organizations need to implement comprehensive information security and resiliency practices for zero trust to be effective. When balanced with existing cybersecurity policies and guidance, identity and access management, continuous monitoring, and best practices, a ZTA can protect against common threats and improve an organization’s security posture by using a managed risk approach.
While there may only be a handful of items active in SAM at this time there are tons of opportunities that contain the tenants of ZTA.
While ZT is the new buzzword in the Cyber market - don't get scooped up in the hype. ZT/ZTA has been around for decades in different forms.
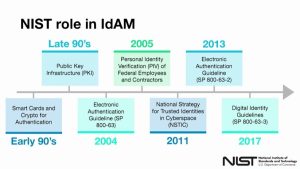
Looking at this image from NIST, I am sure you all remember the early days of PKI and how those soft certs transitioned to the CAC/PIV cards. Identity Management has been a key component of the Defense in Depth architecture that was started in the DoD twenty-five years ago. We don't have any one technology or framework that can totally protect our networks but rather we have to use a variety of tools, processes and frameworks to achieve low risk approaches to supporting the enterprise.
Will Swann
[email protected]
CME, Chief Business Development Officer
571.642.1003